Running an online store comes with many responsibilities, and one of the most important is keeping everything secure.
When websites are not properly protected, hackers can steal customer data, damage your business, or shut your site down.
E-commerce platforms often have hidden weaknesses that attackers look for. Knowing what these security vulnerabilities are helps you stay one step ahead.
This article covers the top 20 types of security vulnerabilities in e-commerce and explains how each one can affect your business.
What are Security Vulnerabilities in E-Commerce?
Security vulnerabilities in e-commerce are weaknesses in online store systems, software, or processes that cybercriminals can exploit.
These flaws may expose customer data, payment information, or internal operations to unauthorized access or manipulation.
Common vulnerabilities include poor authentication, outdated plugins, and unencrypted connections.
Addressing these risks is essential to protect both business operations and customer trust.
Here are several common types of security vulnerabilities found in e-commerce platforms.
Phishing Attacks
Some of the most dangerous threats to online stores start with simple deception.
Phishing attacks involve fake emails, forms, or websites that appear genuine but are designed to steal personal data or login credentials.
These scams target both customers and employees, often leading to major breaches. Phishing is not only a technical risk but also a human one.
Teaching users to recognize suspicious links and using email filters can reduce exposure.
Businesses should invest in anti-phishing tools and implement two-factor authentication for account security.
Understanding these entry points is essential when evaluating the types of security vulnerabilities in e-commerce and how to avoid them.

Credit Card Fraud
Each year, thousands of e-commerce businesses face financial losses due to credit card fraud.
Criminals use stolen card data or spoofed identities to make unauthorized purchases. Fraud often remains undetected until after the consequences have taken effect.
Strong payment gateway integrations, fraud detection systems, and secure checkout protocols are critical.
Monitoring for unusual purchase patterns and verifying card authenticity in real time helps prevent chargebacks.
Protecting payment information should be a top priority for any business operating online.
Account Takeover
It silently begins unauthorized access through stolen login credentials. Account takeover attacks exploit reused passwords or leaked information from other platforms.
Once inside, attackers can steal data, place fraudulent orders, or lock out legitimate users.
Enforcing strict password policies and using multi-factor authentication can help block access attempts.
Security alerts for unusual account activity offer additional defense. In any discussion of types of security vulnerabilities in e-commerce, account takeovers rank among the most disruptive.
Distributed Denial-of-Service (DDoS) Attacks
Large volumes of fake traffic can shut down even the most well-designed website. DDoS attacks overwhelm servers, making the platform inaccessible to genuine users.
This leads to loss of sales, trust, and revenue. Attackers often use botnets to automate these floods, targeting checkout pages or login portals.
A content delivery network (CDN), load balancing, and rate limiting can minimize impact. Constant monitoring helps detect unusual spikes before they grow.
Online businesses should be prepared to handle such threats with proactive planning.

Identity Theft
A customer places an order, unaware that their personal details have already been compromised.
Identity theft occurs when attackers use stolen names, addresses, or payment data to commit fraud.
It not only damages trust but can also trigger legal consequences. Securing data at every step from input to storage is essential.
Avoid collecting unnecessary information and use data encryption methods. Customer verification during high-risk actions adds a layer of protection.
Ensuring the privacy of user data is key to building long-term loyalty.
Fraudulent Returns
Some buyers misuse return policies for profit. Fraudulent returns include sending back fake items, requesting refunds without returning anything, or repeatedly exploiting lenient rules.
While it may seem like a minor issue, return fraud can escalate into major revenue loss.
E-commerce platforms should apply tracking on returns, enforce return conditions, and blacklist frequent offenders.
Automated tools can also flag patterns. Protecting inventory from such abuse requires vigilance and clear policies.
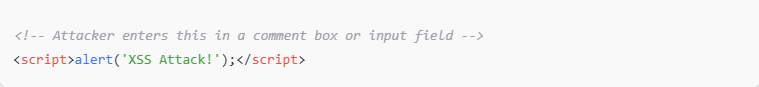
Cross-Site Scripting (XSS)
Imagine a simple comment field turning into a gateway for theft. Cross-site scripting allows attackers to inject harmful scripts into web pages.
These scripts run in the browser of unsuspecting users and can steal cookies, sessions, or personal information.
XSS attacks are often difficult to spot without active scanning. Sanitizing user input, escaping special characters, and using secure coding practices are key defenses.
Regular audits and penetration testing help detect such weaknesses before attackers do. comman example:
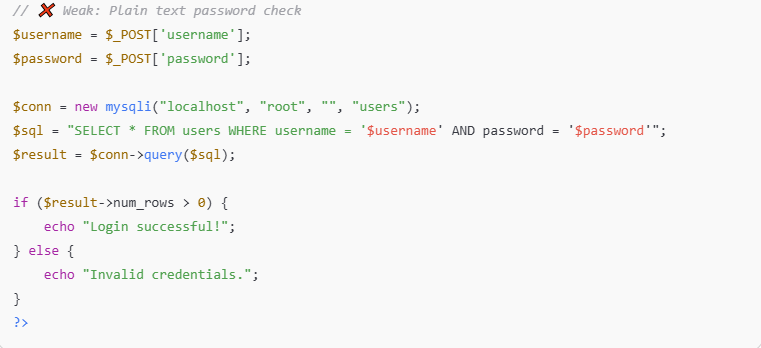
SQL Injection
Databases are the heart of every e-commerce site. SQL injection attacks exploit poorly protected input fields to manipulate or access database contents.
Even a login form can serve as a backdoor if not properly secured. Attackers can retrieve, alter, or delete sensitive data.
To prevent this, websites must use parameterized queries and avoid direct user input in database commands.
Keeping systems patched and monitoring query behavior is also critical.
For example:
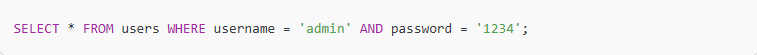
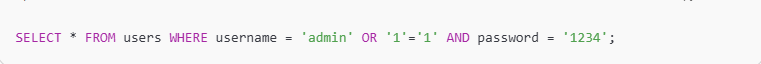
If an attacker enters admin' OR '1'='1 as the username, the resulting query becomes:
Man-in-the-Middle Attacks
Sensitive data like passwords and payment details are often intercepted during transmission.
These attacks happen when hackers insert themselves between the user and the server. If communication is not properly encrypted, attackers can read or alter the data.
Public Wi-Fi networks are common danger zones. Using HTTPS with up-to-date SSL certificates ensures secure communication.
Disabling outdated protocols and implementing certificate pinning further enhances protection.
Insecure Payment Gateways
Payment systems are a frequent target for cybercriminals. A poorly integrated gateway can expose sensitive card data or allow unauthorized transactions.
Weak encryption, poor validation, or outdated plugins all contribute to the problem. It is vital to choose PCI-DSS compliant providers and to test payment flows regularly.
Secure checkout forms, tokenization, and fraud screening can also help reduce risk. An e-commerce site is only as trustworthy as its payment system.

Inventory Hoarding Bots
When products vanish from inventory without real purchases, bots are often to blame.
These scripts add items to carts to manipulate stock levels, skew analytics, or prevent real customers from buying.
Competitors may use this tactic during peak sales periods. Rate limits, CAPTCHA tools, and bot detection software can minimize impact.
Regular stock monitoring and IP filtering are additional defenses. Guarding inventory against non-human traffic helps maintain both sales flow and data accuracy.
Clickjacking
A user thinks they are clicking a normal button, but behind the scenes, something else is happening.
Clickjacking uses hidden frames or deceptive layouts to trick people into performing unintended actions.
This might include sharing private data or activating malware. Frame busting scripts and proper content security policies (CSP) can prevent such manipulation.
Always test interfaces for visual integrity across devices and browsers to reduce this threat.
Unpatched Software or CMS Plugins
A single outdated plugin can become a major liability. Attackers actively scan for known vulnerabilities in CMS platforms and e-commerce plugins.
If updates are skipped, even minor flaws can become dangerous. Automating patch updates, removing unused extensions, and subscribing to security alerts are effective steps.
Security is not a one-time setup; it requires ongoing maintenance to remain effective.
Insecure APIs
Application programming interfaces (APIs) connect websites with payment processors, shipping services, and other tools.
If these are not properly secured, attackers can bypass the main site and access backend systems.
Common risks include missing authentication, data leakage, and exposure to injections. API security should include access tokens, encryption, and request validation.
Regular API monitoring helps detect misuse or unauthorized activity.
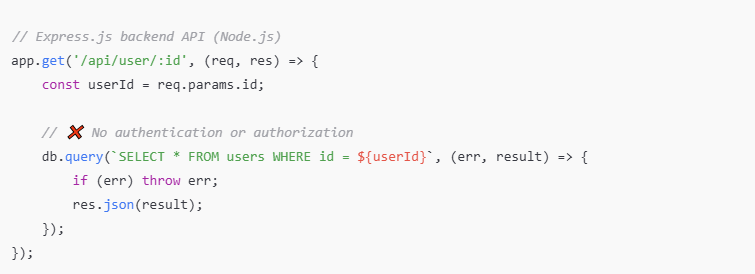
Weak Authentication
Simple passwords and lack of verification allow attackers easy access to customer or admin accounts.
Weak authentication systems are often the first point of failure. Strengthening login procedures with multi-factor authentication, password complexity rules, and login attempt limits can reduce the chance of unauthorized access.
Monitoring login activity and implementing device recognition offer additional protection layers.
Malware and Ransomware
A single malicious file can lock down an entire store. Malware infiltrates systems through compromised plugins, email attachments, or fake updates.
Ransomware then encrypts critical data and demands payment to restore access.
Keeping backups, installing real-time threat detection tools, and restricting file uploads are all effective safeguards. Employee training also helps prevent accidental installations.
Insider Threats
Internal actors, like employees or contractors, can pose risks that are difficult to detect. They may leak data, misuse access rights, or sabotage systems.
Regular audits of user permissions, background checks, and activity monitoring help reduce these threats.
A clear access control policy ensures that employees only reach the data they need. Minimizing insider risks is essential in any e-commerce security strategy.
Compliance Gaps
Failure to comply with data protection regulations can result in fines and damage to trust.
If it is PCI-DSS for payment data or GDPR for user privacy, staying compliant protects both the business and its customers.
Conducting periodic compliance checks and working with legal experts helps prevent unintentional violations.
Transparency with users about data collection and use is also important for maintaining credibility.
Weak Encryption
If communication is not properly encrypted, user data can be intercepted. Weak or expired SSL certificates put login credentials, payment data, and personal information at risk.
Use strong encryption standards, ensure certificates are valid, and avoid outdated algorithms.
Always test encryption across all entry points, including forms, APIs, and mobile versions of your site.
Fake Online Stores
Some attackers create lookalike websites to trick users into entering their information.
These scam sites can collect payments without delivering products or installing malware.
Protecting your brand name, using trust seals, and encouraging direct links from verified sources help prevent impersonation.
Reporting fake sites promptly also reduces their lifespan.
Effective Tips for E-Commerce Fraud Mitigation
Below are essential measures to reduce risk. Adopting a proactive approach ensures a safer environment for your customers and a stronger foundation for your business.
Implement Multi-Factor Authentication (MFA)
Adding more than one step to the login process makes it harder for attackers to gain unauthorized access.
Multi-factor authentication requires users to verify their identity using something they know and something they have, like a phone or app code.
This extra layer blocks most brute-force and credential-stuffing attempts.
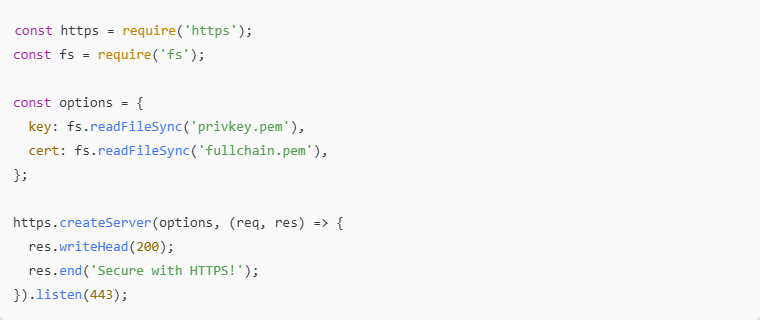
Use HTTPS and Strong SSL Certificates
Encrypting all communication between users and the server helps prevent data from being intercepted.
HTTPS, backed by valid SSL certificates, is essential for protecting login pages, checkout processes, and personal information.
Renew certificates regularly and disable outdated encryption protocols for better security.
duct Regular Vulnerability Assessments
Security threats change constantly. Performing scheduled vulnerability scans helps detect new risks in your systems, code, or integrations.
Assessments identify weak spots before attackers do, making it easier to fix them promptly and maintain a secure environment for your users.
Keep Software and Plugins Up to Date
Outdated software often contains known flaws that cybercriminals can easily exploit.
Make sure to update your content management system, themes, plugins, and server components regularly.
Unused plugins or extensions should be removed to reduce potential entry points.
Use AI-Driven Fraud Detection Systems
Modern fraud detection tools use artificial intelligence to spot suspicious activity patterns.
These systems can flag high-risk transactions, block bots, and reduce false positives more effectively than manual checks.
Real-time monitoring gives businesses a better chance to respond to emerging threats.
Following are some AI-driven fraud detection systems:
Sift
Sift uses real-time machine learning to analyze user behavior, device fingerprints, and transaction history.
It assigns a risk score to each activity and helps prevent account takeovers and payment fraud.
E-commerce platforms often use it to automate fraud decisions. Its adaptable model evolves as new threats appear. Sift also offers detailed case management tools.
Forter
Forter provides instant fraud decisions based on AI and a global merchant network. It focuses on reducing friction for legitimate users while blocking fraud in real time.
It supports identity verification, abuse prevention, and chargeback protection. Forter’s system learns from every transaction across its network to improve accuracy.
It is widely adopted in fashion, travel, and digital goods.
Kount (by Equifax)
Kount leverages AI and device intelligence to detect fraud before it happens.
Its Identity Trust Global Network helps understand user behavior across thousands of websites.
Kount offers real-time decision-making for payments, logins, and account creation.
It also allows businesses to customize rules and thresholds. Ideal for scalable fraud prevention.
Riskified
Riskified is designed for e-commerce and specializes in chargeback prevention.
It uses machine learning to assess each transaction’s legitimacy in milliseconds.
The system guarantees transactions it approves, reducing financial risk. It integrates easily with major e-commerce platforms.
Riskified helps merchants increase approval rates and protect revenue.
Feedzai
Feedzai’s platform is built for banks and fintechs to detect fraud in real time.
It uses AI to analyze transactions, customer profiles, and device usage patterns.
It offers a risk engine, visual investigation tools, and customizable workflows. Feedzai supports both online and offline channels.
It is highly scalable and suits large financial institutions.
Educate Staff and Customers on Phishing and Social Engineering
Human error remains one of the biggest security challenges. Training employees to recognize fake emails, urgent scam messages, or unusual behavior is vital.
Customers should also be informed about how to securely interact with your website. Awareness reduces the chances of successful social engineering attacks.
How Can BrandOutAdv Secure Your ECommerce Platform?
BrandOutAdv secures your e-commerce platform through custom development services designed with security at their core.
Every feature, from user login systems to payment integrations, is built using clean, secure code that reduces risk from the start.
BrandOutAdv ensures that your online store is not only functional and scalable but also protected against threats like data breaches, payment fraud, and unauthorized access.
Regular updates, secure APIs, and compliance-ready structures are all part of the custom development approach that keeps your platform safe and reliable.
Ending lines
E-commerce security is not something to take lightly. Every security vulnerability in E-commerce, no matter how small, can lead to serious damage, lost data, stolen payments, or broken customer trust.
Understanding these common threats and applying the right protection methods, businesses create safer online shopping experiences.
Regular updates, strong authentication, staff training, and secure payment systems all play a part.
Staying alert and proactive is the best way to protect your platform. Taking these steps today can help prevent costly problems tomorrow and keep your business running smoothly.
Most asked questions:
What are the major security issues in e-commerce?
Some major security issues in e-commerce include phishing attacks, credit card fraud, account takeovers, data breaches, and insecure payment systems.
These threats can lead to stolen customer information, financial losses, and damage to the business’s reputation.
What is a security breach in cyber security?
A security breach happens when someone gains unauthorized access to data, networks, or systems.
In cyber security, this could mean hackers stealing personal information, financial records, or login details from a company or its users.
Why does e-commerce security matter?
E-commerce security is important because it protects customer data, prevents financial fraud, and keeps online stores running smoothly.
Without strong security, businesses risk losing trust, facing legal problems, and suffering major losses.
What is one of the biggest threats of online shopping?
One of the biggest threats of online shopping is identity theft.
Cybercriminals can steal personal and payment information to make fake purchases or commit fraud, often without the customer even knowing until it is too late.